keystash
v1.0.8
Published
Store secrets in S3 using KMS envelope encryption.
Downloads
16
Maintainers
Readme
🔑💌 keystash
Save secrets in AWS S3 with KMS envelope encryption
- Save key/value pairs in an S3 Bucket with KMS envelope encryption
- Additional serverside encryption with S3
- Automatic S3 versioning for durability
- Generate random key data
- Use as a module
- Bundles a simple CLI
Perfect for:
- Centralized key management with minimalist command line interface
- Environment variables in modules and npm scripts
- Lightweight and secure personal key value store
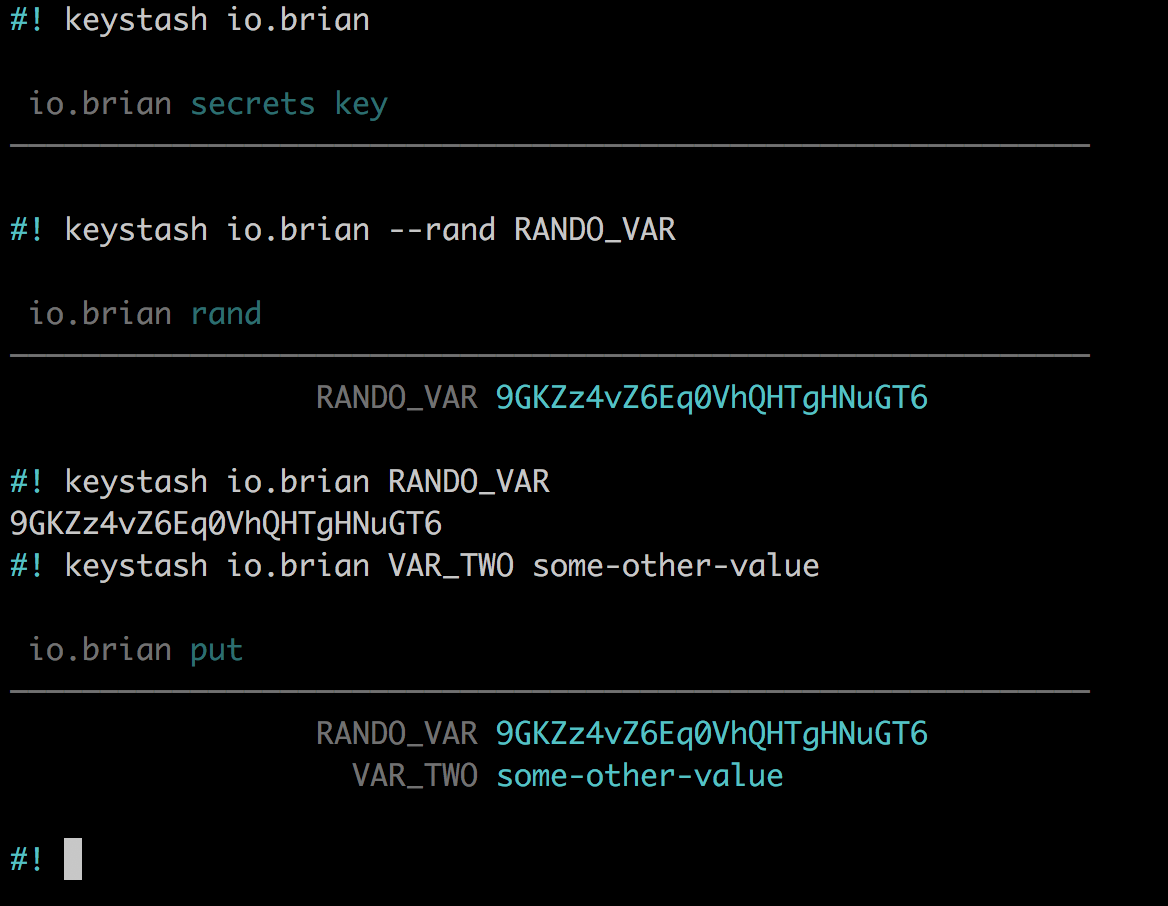
prereq
- AWS account credentials setup
.aws/credentials AWS_PROFILEandAWS_REGIONenvironment variables
✨ Tip
exportdefaultAWS_PROFILEandAWS_REGIONenv vars your in.bashrcor.bash_profileand override as neccessary on the command line or inpackage.jsonto make working with different stashes easy
install
npm i -g keystashcommand line interface
keystash <bucket name> [options]exmaples
Setup an S3 bucket:
keystash my-bucket --createcreate an S3 bucket for storing secrets
Read secrets:
keystash my-bucketread encrypted secrets from S3 bucketkeystash my-bucket BIG_SEKRETto read a value to stdout
Write secrets:
keystash my-bucket BIG_SEKRET xxx-xxxsave a secretBIG_SEKRETwith valuexxx-xxxkeystash my-bucket --rand BIG_SEKRETto generate (really!) random key datakeystash my-bucket --delete BIG_SEKRETremoveBIG_SEKRETkeystash my-bucket --resetremove all secrets from latest version
Working with versions:
keystash my-bucket --versionslist all versionskeystash my-bucket --versions some-version-idget secrets for a given versionkeystash my-bucket --versions some-version-id some-keyget the key for the given versionkeystash my-bucket --nukeremove all versions
Run keystash --help to see short switches.
module install and usage
Use this module in npm scripts.
npm i keystash --save// package.json
{
"start": "DB_URL=${keystash some-bucket DB_URL} node index"
}Or a bash script:
AWS_PROFILE=xxx
AWS_REGION=xxx
NODE_ENV=testing
DB_URL=`keystash cred-bucket DB_URL`
node indexOr in module code itself:
var keystash = require('keystash')
keystash.read({ns: 's3-bucket-name'}, console.log)See tests for more examples!
api
var keystash = require('keystash')keystash.create({ns}, err=>)create akeystashS3 bucketkeystash.delete({ns, key}, (err, result)=>)remove a keykeystash.env({ns}, err=>)add secrets toprocess.envkeystash.nuke({ns}, err=>)remove all versionskeystash.rand({key}, (err, result)=>)generate a random keykeystash.read({ns}, (err, result)=>)get all secretskeystash.read({ns, version}, (err, result)=>)get all secrets for given versionkeystash.reset({ns}, (err, result)=>)remove all secrets from the current versionkeystash.versions({ns}, (err, result)=>)get all versionskeystash.write({ns, key, value}, (err, result)=>)save a secret
acknowledgements
This module is inspired by credstash. This module differs in that its JavaScript instead of Python and uses S3 to persist secrets instead of Dynamo. Read more about credstash here.
Also thx to Matt Weagle for encouraging KMS envelope encryption and Ben Kehoe for suggesting to use the S3 Object Metadata property to store the KMS cipher.
